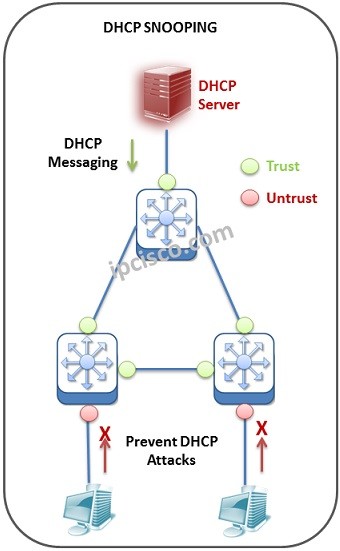
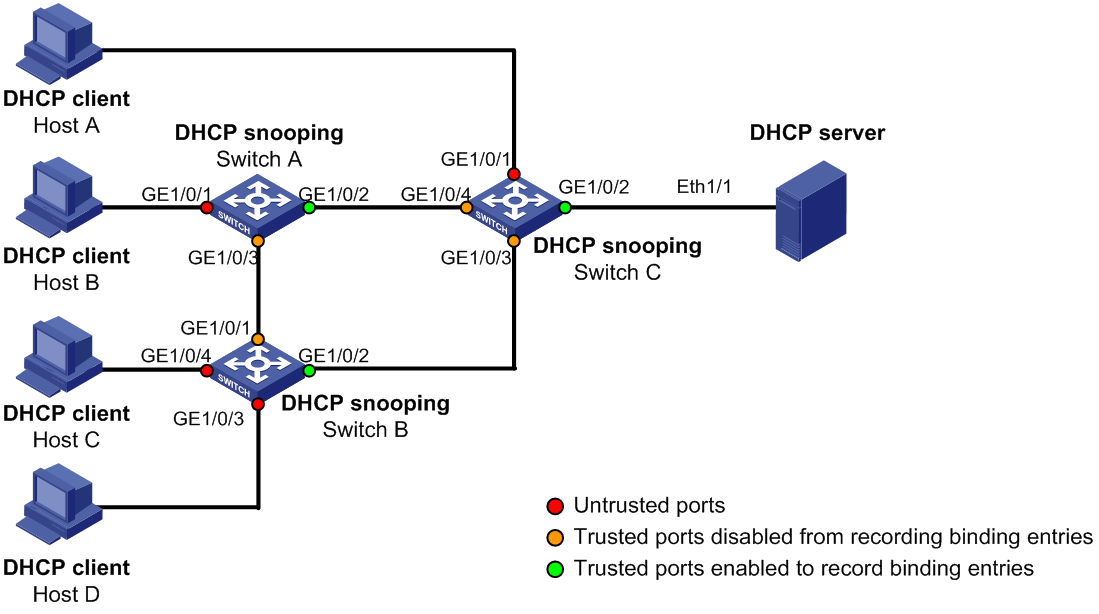
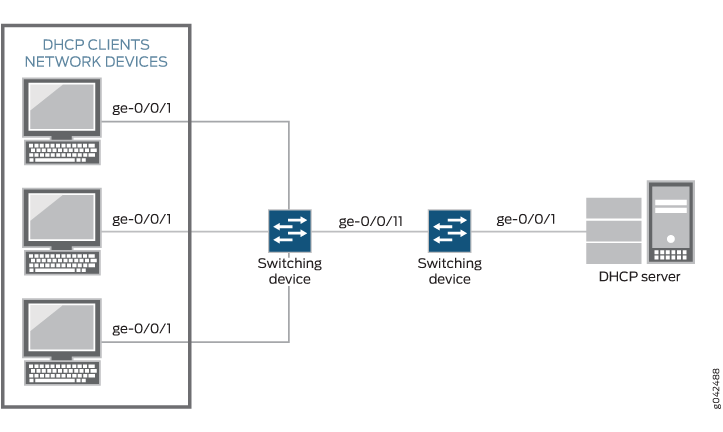
Juniper Networks :: Technical Documentation :: Example: Configuring DHCP Snooping, DAI , and MAC Limiting on an EX Series Switch with Access to a DHCP Server Through a Second Switch

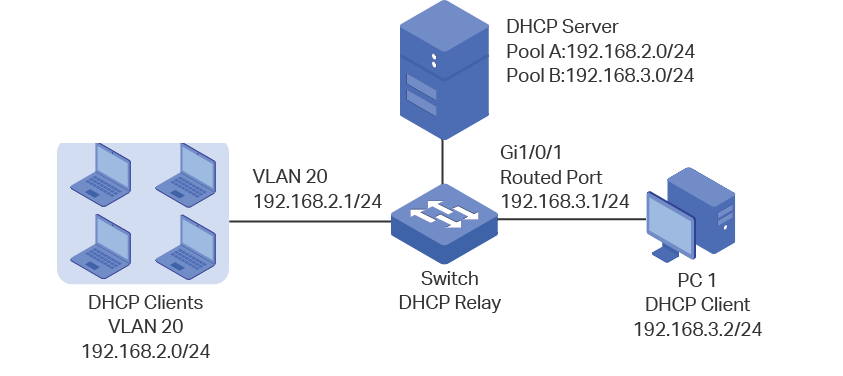
Example: Configuring Port Security, with DHCP Snooping, DAI, MAC Limiting, and MAC Move Limiting, on an EX Series Switch
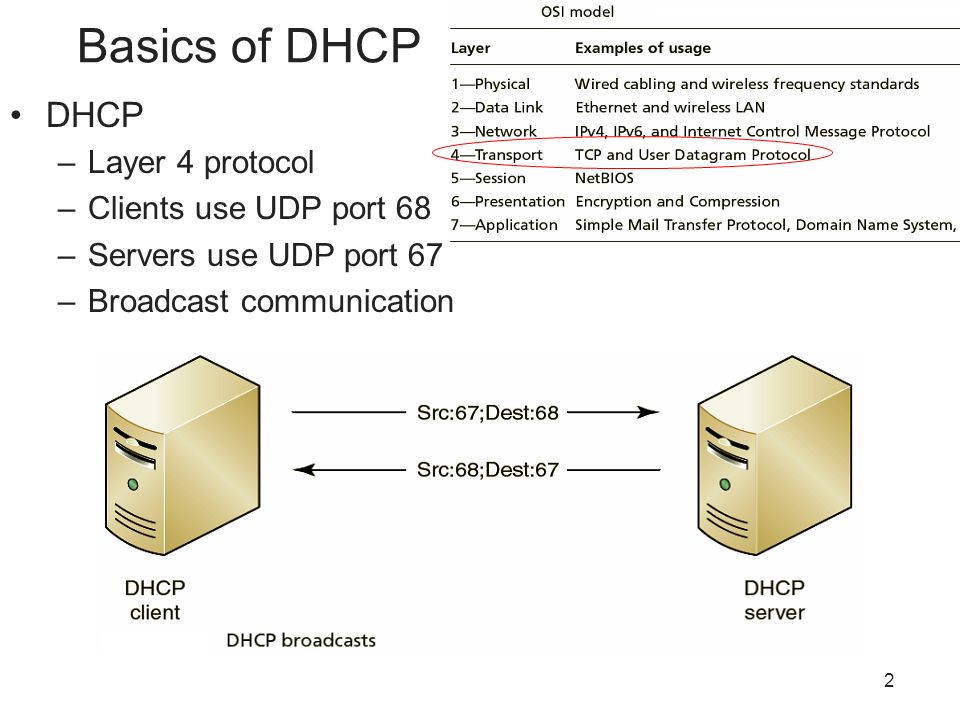
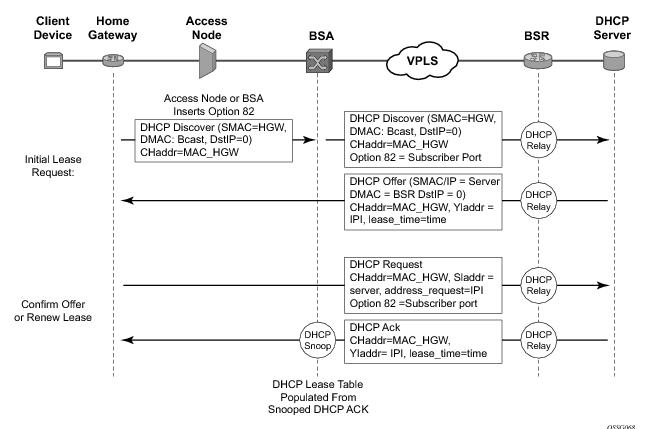
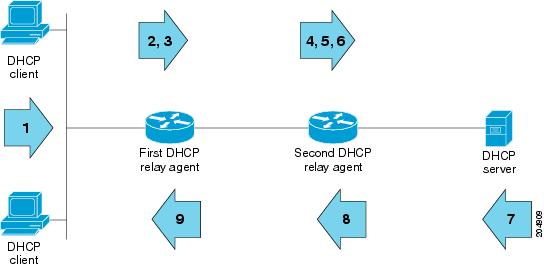
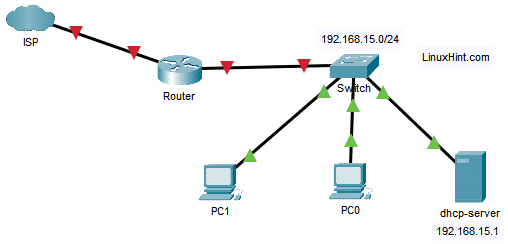
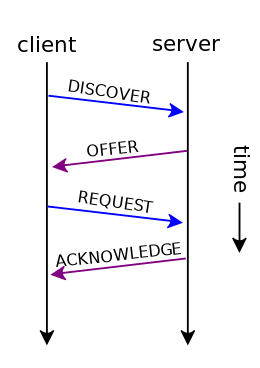
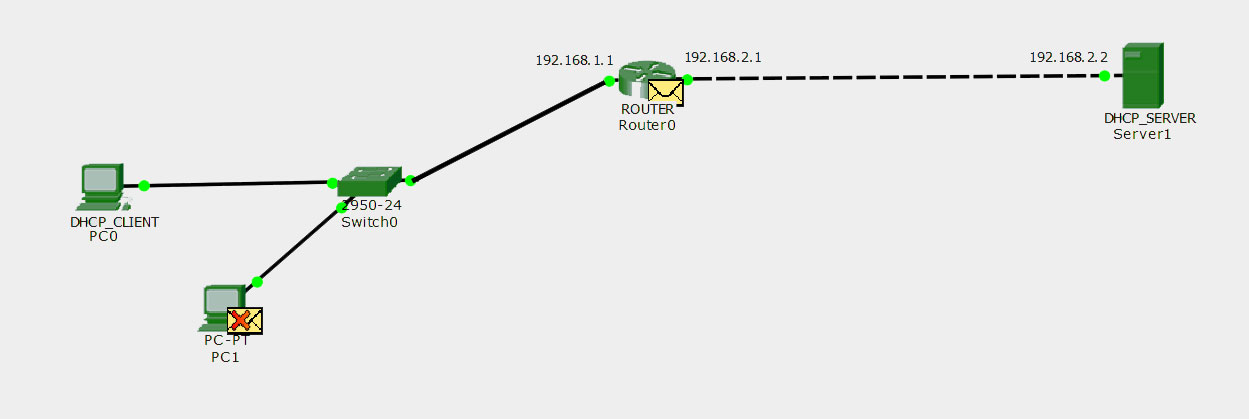

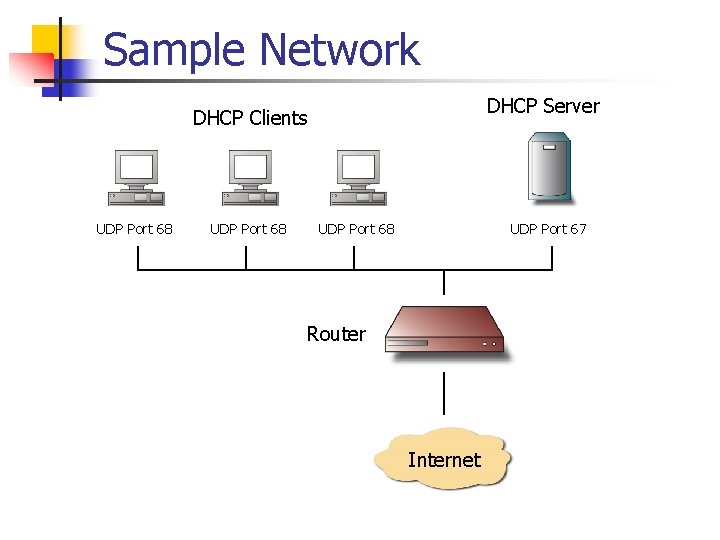
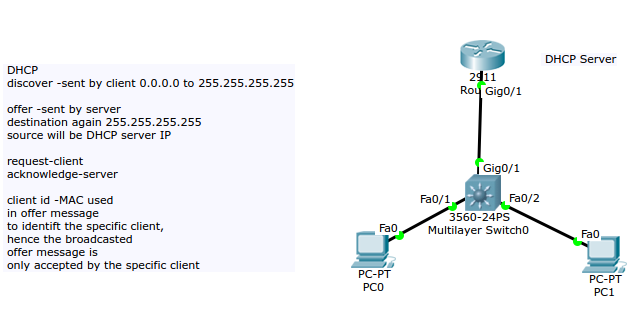

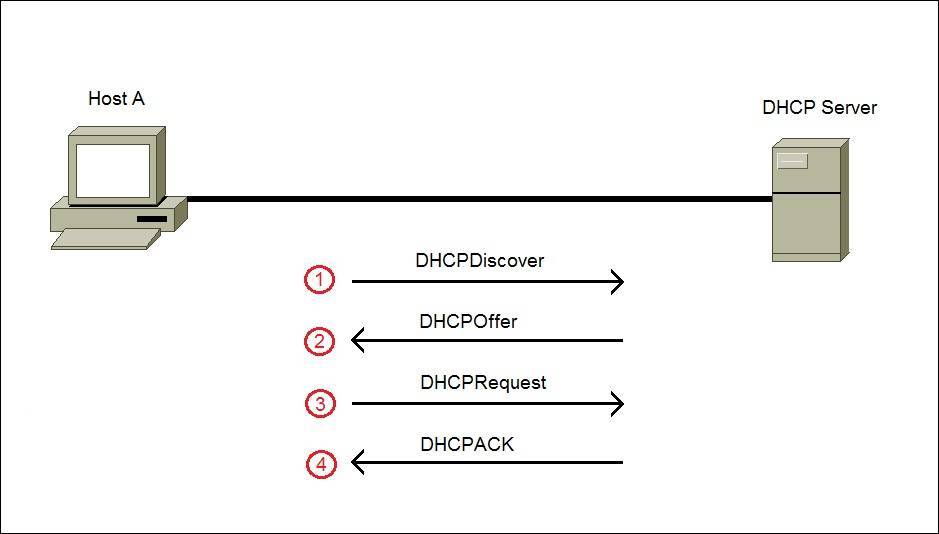
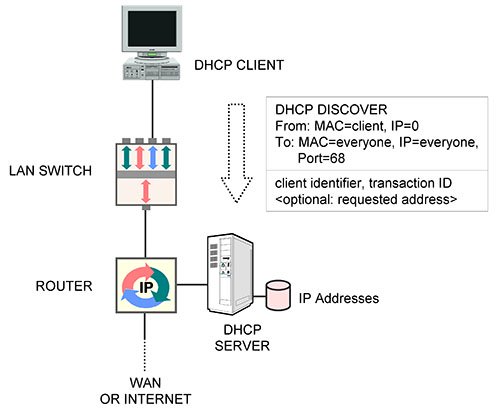
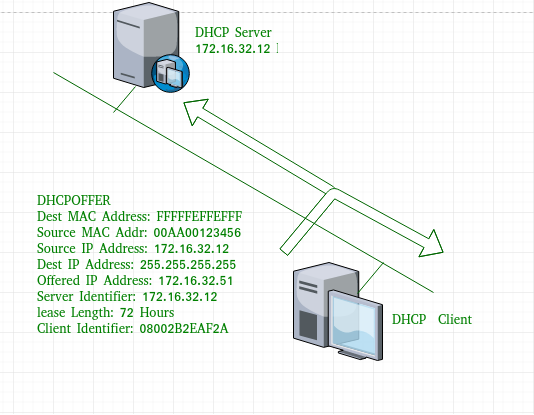



![The DHCP process - CCNA Security 210-260 Certification Guide [Book] The DHCP process - CCNA Security 210-260 Certification Guide [Book]](https://www.oreilly.com/library/view/ccna-security-210-260/9781787128873/assets/530ee9b6-d3af-46a0-9189-f8bfacd00b8e.jpg)